OWASP CSRFGuard

The OWASP CSRFGuard is one of the world’s most popular free security tools and is actively maintained by a pool of international volunteers.
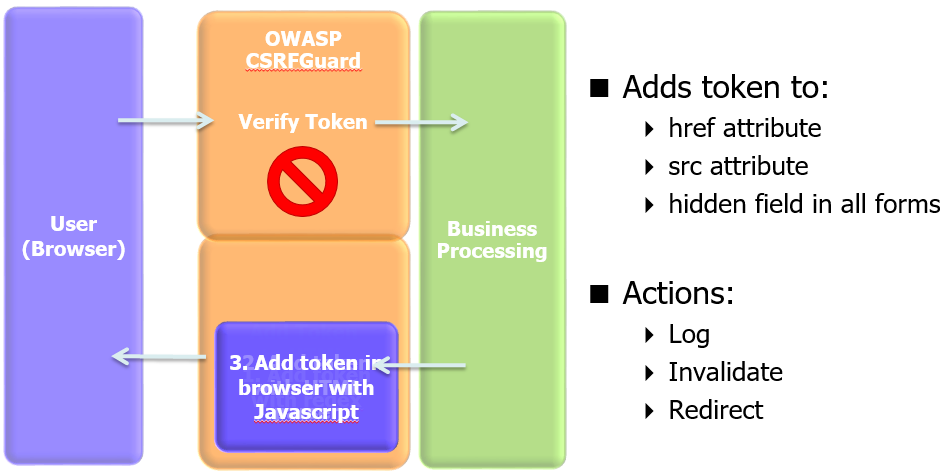
Welcome to the home of the OWASP CSRFGuard Project! OWASP CSRFGuard is a library that implements a variant of the synchronizer token pattern to mitigate the risk of Cross-Site Request Forgery (CSRF) attacks.
The OWASP CSRFGuard library is integrated through the use of a JavaEE Filter and exposes various automated and manual ways to integrate per-session or pseudo-per-request tokens into HTML. When a user interacts with this HTML, CSRF prevention tokens (i.e. cryptographically random synchronizer tokens) are submitted with the corresponding HTTP request.
It is the responsibility of OWASP CSRFGuard to ensure the token is present and is valid for the current HTTP request.
Any attempt to submit a request to a protected resource without the correct corresponding token is viewed as a CSRF attack in progress and is discarded. Prior to discarding the request, CSRFGuard can be configured to take one or more actions such as logging aspects of the request and redirecting the user to a landing page. The latest release enhances this strategy to support the optional verification of HTTP requests submitted using Ajax as well as the optional verification of referrer headers.
As OWASP project we follow the OWASP Code Of Conduct available here: https://owasp.org/www-policy/operational/code-of-conduct
OWASP CSRFGuard 4.0.0
Some CSRGuard features
Tags
<img src=“https://bank.com/fn?param=1”>
<iframe src=“https://bank.com/fn?param=1”>
<script src=“https://bank.com/fn?param=1”>
Autoposting Forms
<body onload="document.forms[0].submit()">
<form method="POST" action=“https://bank.com/fn”>
<input type="hidden" name="sp" value="8109"/>
</form>
XmlHttpRequest
Subject to same origin policy
Credentials Included
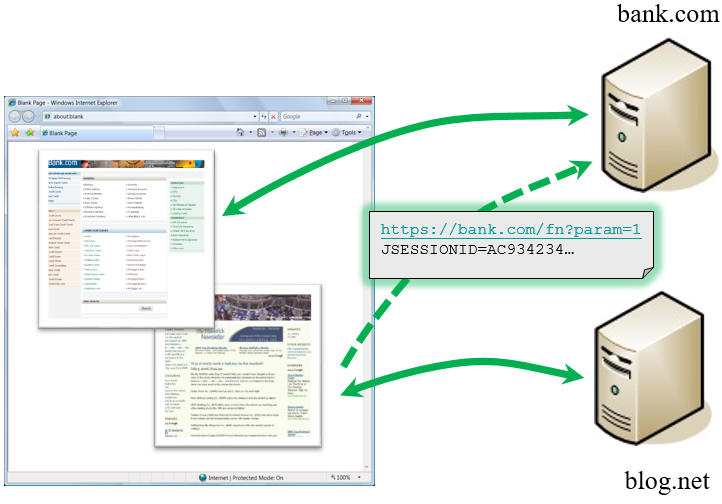
How Does CSRF Work?
What is CSRF (Cross-Site Request Forgery) Attacks
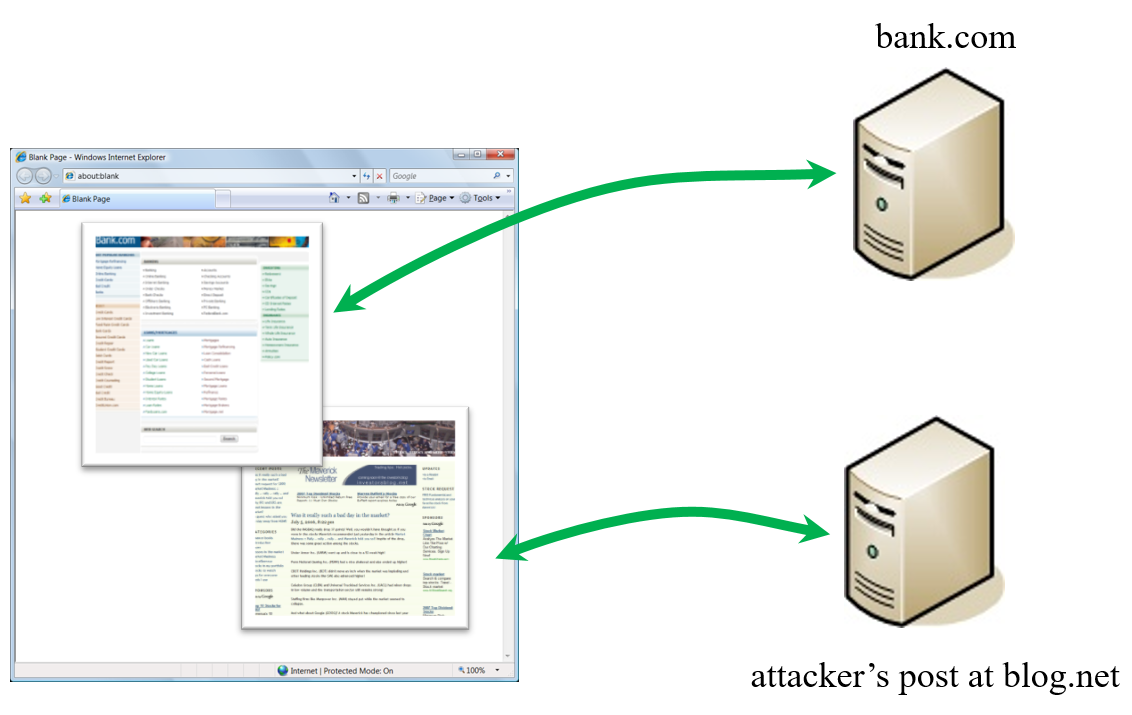
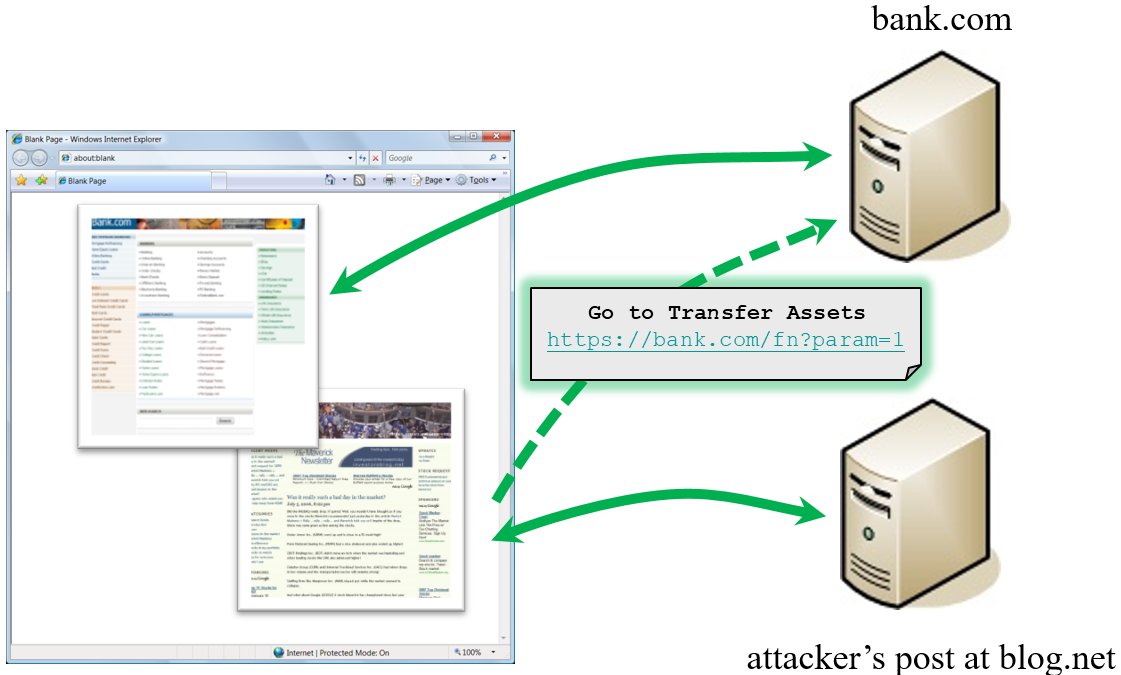
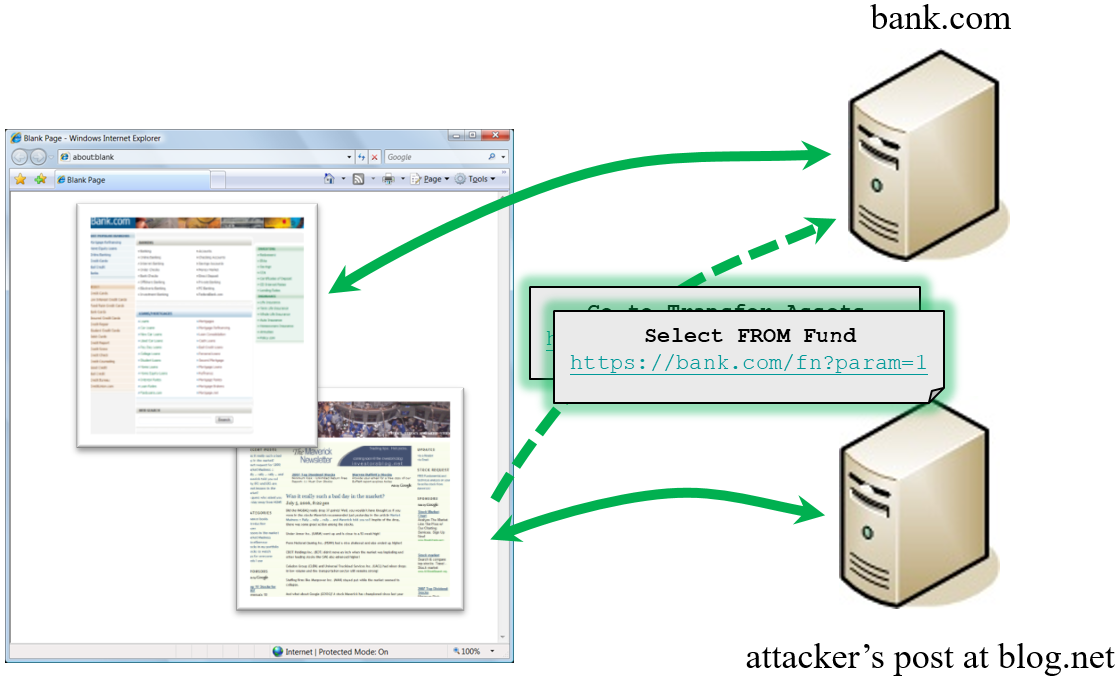
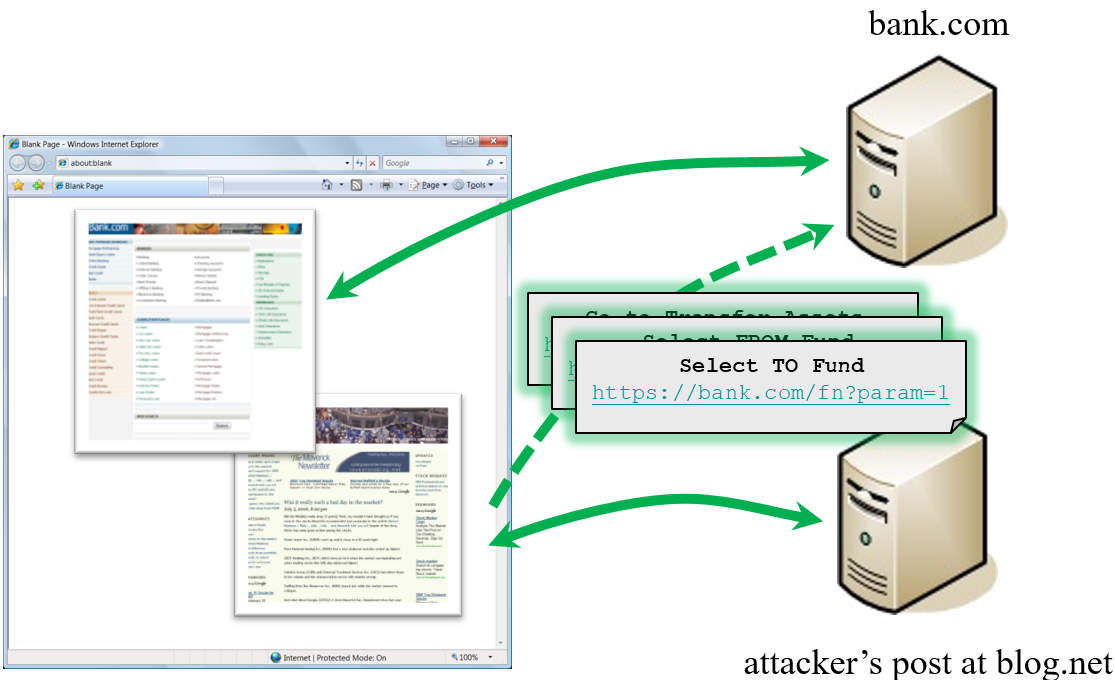
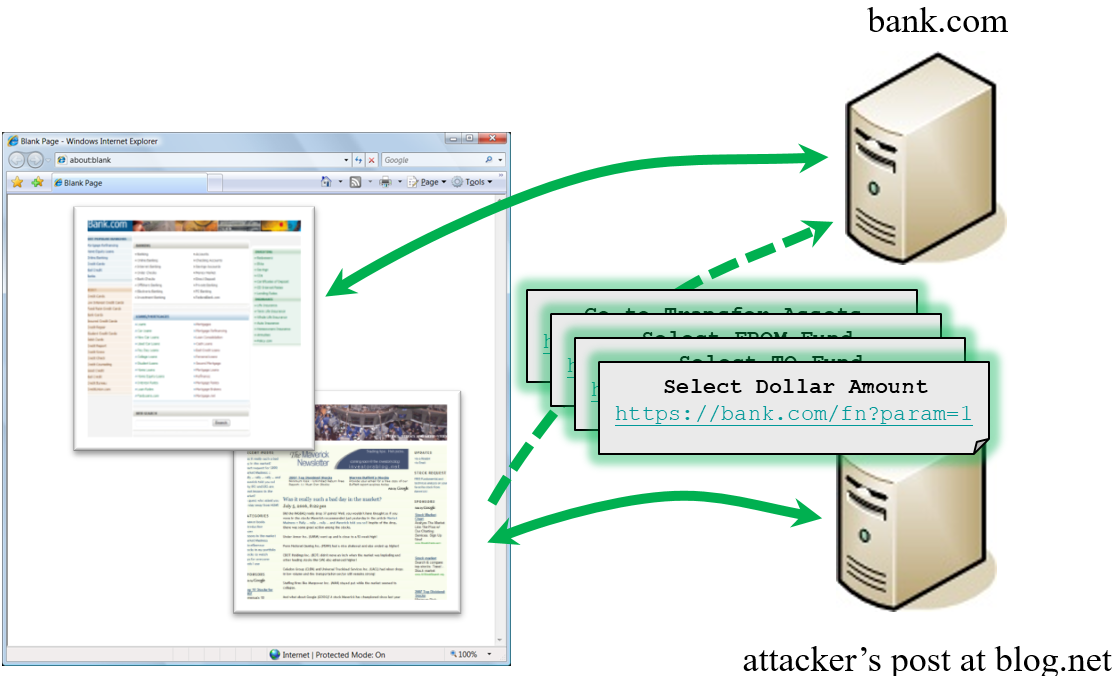
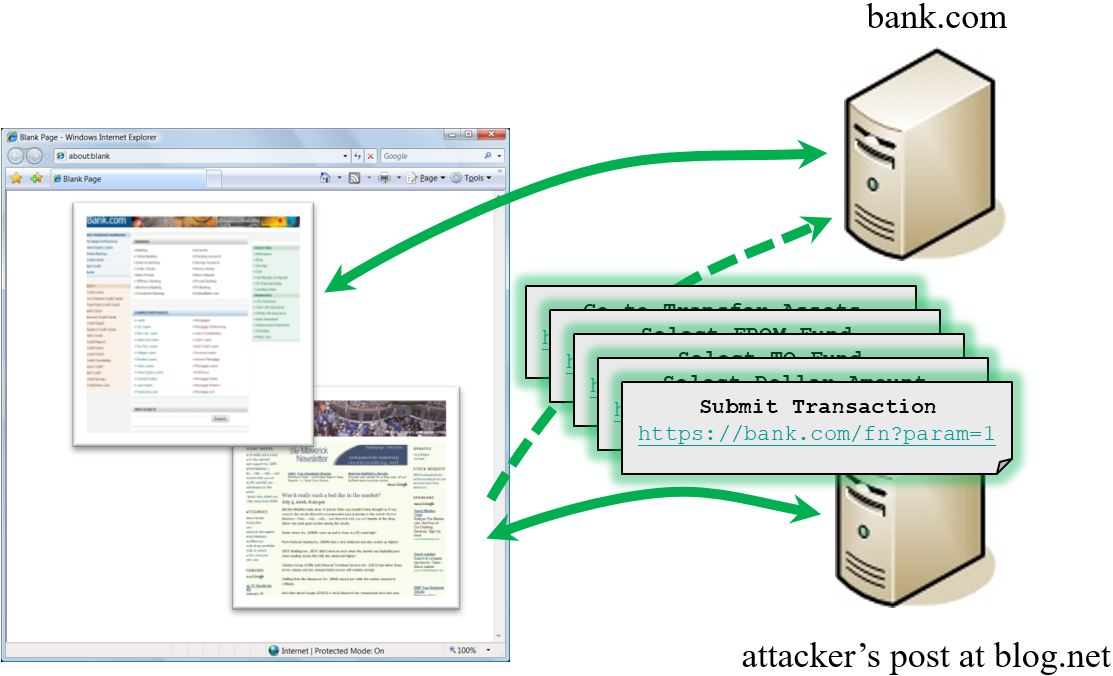
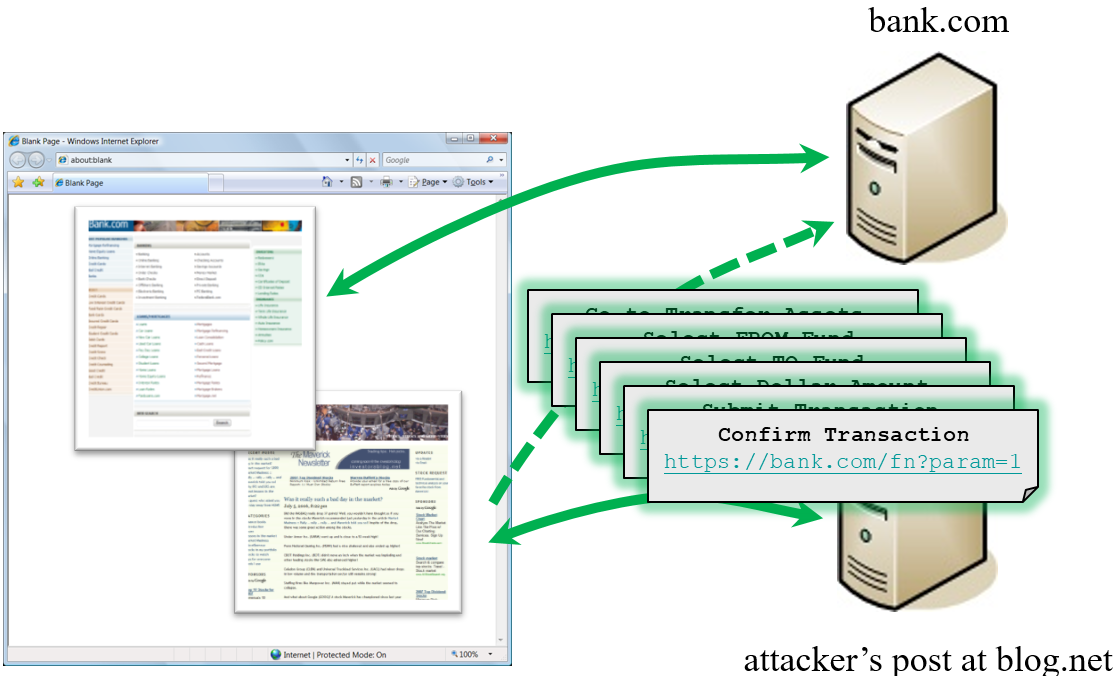
CSRFGuard In Action
Latest News
We are working on a new version of CSRFGuard including a lot of merge request with good proposals and new code to fix known issues on XSS attacks that bypass CSRFGuard.
Target date for the new release 4.0 : 2021
We need your help. If you want to give few hours of your time please reach out to us.
Supporters
CSRFGuard is developed by a worldwide of volunteers in Morocco, France, India, China, Singapore, Indonesia, Canada and more.
Special Thanks
Thanks to Trent Schmidt and Joel Orlina (JIRA) for there help.
Documentations for various Web Application Servers
We need first to create a complete set of installation guide for various Java Application Server.
CSRFGuard 4.0 features
CSRFGuard 4.0 is under development. If you are Java developer and want to help as OWASP volunteer please contact the project leaders. We will remove all CSRFGuard 3.1.0 limitations and release CSRFGuard 4.0
The following roadmap will remove the following CSRFGuard 3.1.0 limitations:
- CSRF Guard utilizes the external interface of Tomcat web server; it may not provide adequate protection for other web server applications (e.g. Internet Information Server IIS).
- CSRF Guard can provide adequate protection against CSRF attacks; however, it can be compromised by server side vulnerabilities such as cross site scripting or client side vulnerabilities (session hijacking or clickjacking) or unintentional leverage token by unauthorized parties.
- CSRF Guard makes the connection between a token and a session id to check the token validity, Because of this dependency on the session identifiers; it cannot defend against login CSRF attacks.
- CSRF Guard filters input HTTP requests by token pattern; therefore, it cannot check the input validation error, to effectively protect against CSRF attack, the developer needs to ensure the web application implements countermeasures to defense against cross scripting attacks.
- Enhance Token Injection Process
- Add protection against Clickjacking
- Add protection against Session Hijacking bypassing CSRFGuard
- Add protection against XSS by passing CSRFGuard